Standards have always been the guiding principles that ensure products and services are offered to clients securely and reliably. These standards, often enforced by organizations saddled with the responsibility by law, keep industries in check and prevent the proliferation of substandard products. In the IT industry, maintaining standards goes beyond shipping a final product to clients; doing so covers the entire lifecycle of the solutions offered. Every industry uses technology in various forms to move fast and drive results efficiently, leading to the creation, storage, and transfer of massive amounts of data, which are often sensitive. Mishandling of data can cause significant damage, to the tune of hundreds of millions of dollars.
In a recent blog post, researchers at the International Monetary Fund (IMF) shared that the COVID-19 pandemic accelerated the adoption of digital technologies, shielded productivity across the globe from the impact of the pandemic and saw an increase in labor force participation in countries where working from home is more common. Contact-intensive sectors also sought innovative, mostly technology-based solutions to reduce exposure to the COVID-19 virus. This acceleration came with challenges, a rise in software supply chain security incidents, and data protection issues. Compliance and security policy management has never been more important, as companies want to ensure standard operating procedures, whether self-imposed or imposed by a regulatory body, are adhered to.
Common IT compliance standards
Regulatory compliance standards come in various forms and depend on the industry or region an organization operates in. Common compliance standards include the following:
- HIPAA: The Health Insurance Portability and Accountability Act of 1996 in the U.S. creates standards to protect patient information from disclosure without consent
- GDPR: General Data Protection Regulation is a European Union data privacy and security law, which applies to all companies across the globe that process the personal data of EU citizens or residents.
- NIST SSDF: The Secure Software Development Framework, created by the U.S. National Institute of Standards and Technology (NIST) as standards and best practices for secure software development.
- PCI DSS: Information security standards for financial institutions that process payments, especially with credit cards. PCI DSS is administered by the Payment Card Industry Security Standards Council.
Aside from widely recognized standards, countries often have standards specific to their citizens or region and organizations are obliged to comply if they wish to operate in those regions.
Compliance management
Organizations are mandated to meet standards or risk fines or legal action. Some organizations even go above and beyond to set more stringent standards for themselves to maintain a reputation and build trust with clients. To meet standards, compliance metrics must be evaluated and integrated into standard operating procedures to provide insights that enable early detection and prevention of current and future compliance risks. Thus, the need for efficient compliance management.
Compliance management with GitLab
According to the 2023 GitLab Global DevSecOps Report, surveyed respondents mentioned continuous compliance as a key factor in ensuring the efficiency and security of their software development lifecycle. GitLab provides features that allow organizations to create compliance frameworks, security policies, and audit management. GitLab also enables compliance or leadership teams to monitor compliance metrics with compliance reports. Let's take a look at some of these features.
Compliance frameworks and pipelines
Organizations can create a compliance framework that identifies projects that need to meet defined compliance requirements, which can be enforced with compliance pipelines. For example, a FinTech company can create a default compliance framework for all projects, ensuring every stage of their software development lifecycle meets the PCI DSS requirements for handling cardholder data.
These requirements are then enforced by ensuring every change introduced to the codebase is sufficiently tested automatically with GitLab’s application security features, which cover source code, as well as dependencies, and vulnerabilities in running application and infrastructure configurations. You can learn more about how GitLab helps you achieve PCI compliance and other regulatory compliance with compliance frameworks.
The following video demonstrates setting up and using compliance frameworks and pipelines.
Security policy management
Security and compliance teams can use GitLab to enforce compliance requirements by ensuring security scanners run in pipelines where necessary or by requiring approval on merge requests when security policies are violated. GitLab supports scan execution and scan result policies. These policies are defined in a dedicated security policy project that establishes a separation of duties between security and development teams. Security policies can be applied granularly at the group, sub-group, and project levels. The policies can be edited in rule mode, which uses the policy editor or by using yaml mode.
Scan execution policies
Scan execution policies can be configured to run a SAST, SAST IaC, DAST, secret detection, container, or dependency scan on a specified GitLab runner. The scan jobs can be run on schedule, or anytime a pipeline runs. Compliance and security teams can use scan execution policies to periodicailly check on and proactively prevent escalation of vulnerabilities. They can also be used to reinforce controls when new trends are observed from scan results.
Scan result policies
Scan result policies add required review and approval of merge requests when the results of specified security scans violate the policies' rules. For example, a policy can require a security team member to take action when a newly identified critical SAST vulnerability is detected. This way, security and compliance team members can support developers while ensuring the changes introduced to the codebase are secure and meet compliance requirements.
License approval policies
When selecting scan types for scan result policy rules, you have the option of security scan, the default behaviour for scan result policies, and license scan. License scanning depends on the output of the dependency scanning CI/CD job to check if identified licenses match specified criteria, then adds approval requirements before an open merge request can be merged. This is crucial to ensure that only dependencies with approved licenses are used in your organization.
Audit management
Understanding the security and compliance posture of your organization is an important part of compliance management. You want to be aware of every action taken on the GitLab instance with audit events, which allows you to track every important event, who performed it, and when. You can also generate detailed reports from audit events using audit reports, allowing you to prove your compliance to auditors or regulators.
Compliance reports are a major component of audit management in GitLab, giving visibility to the compliance posture of your organization. Compliance reports detail every violation discovered with the violations report and the frameworks used by projects within your organization with the compliance frameworks report.
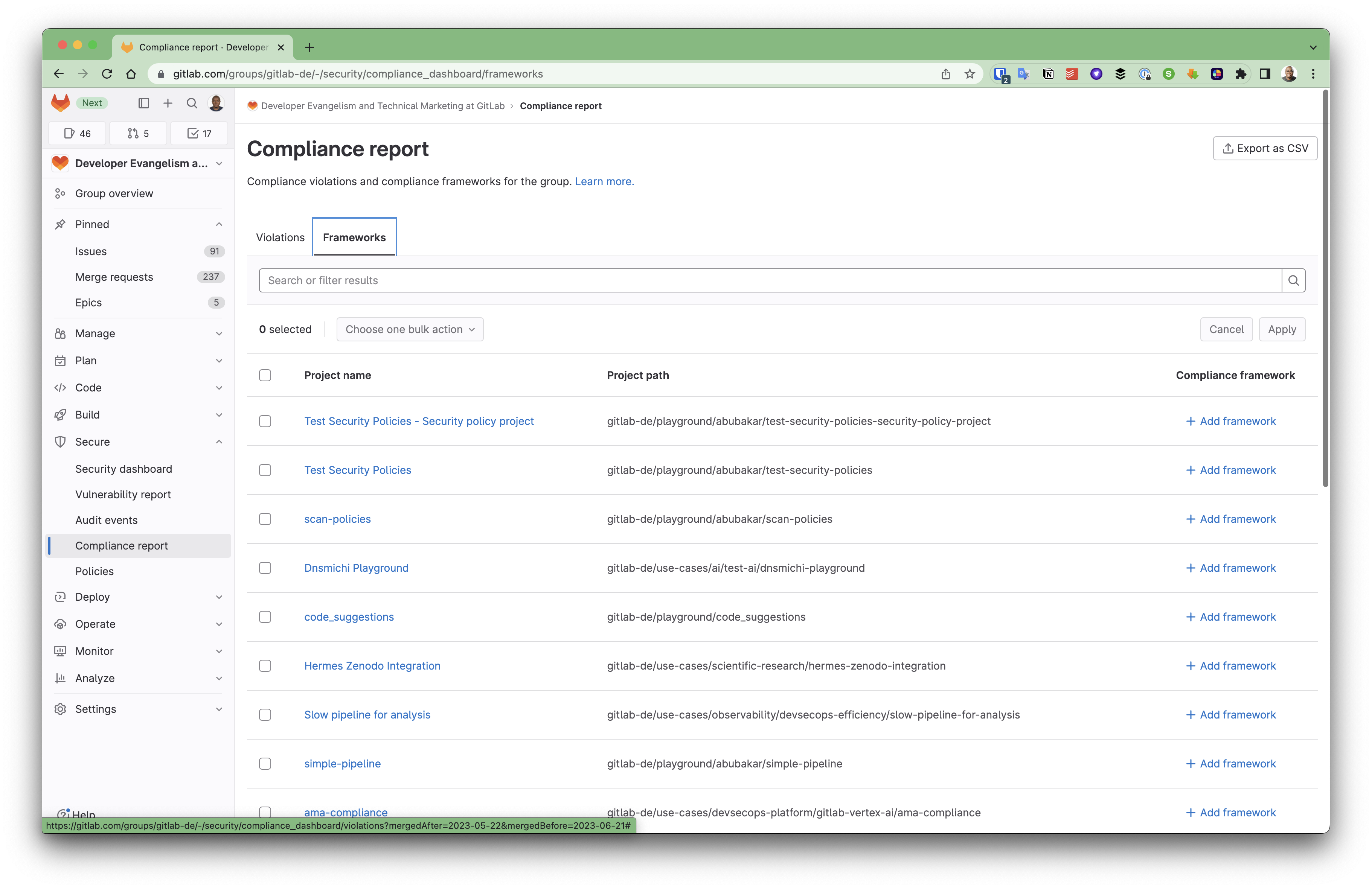
An example of compliance violations report from a parent GitLab group
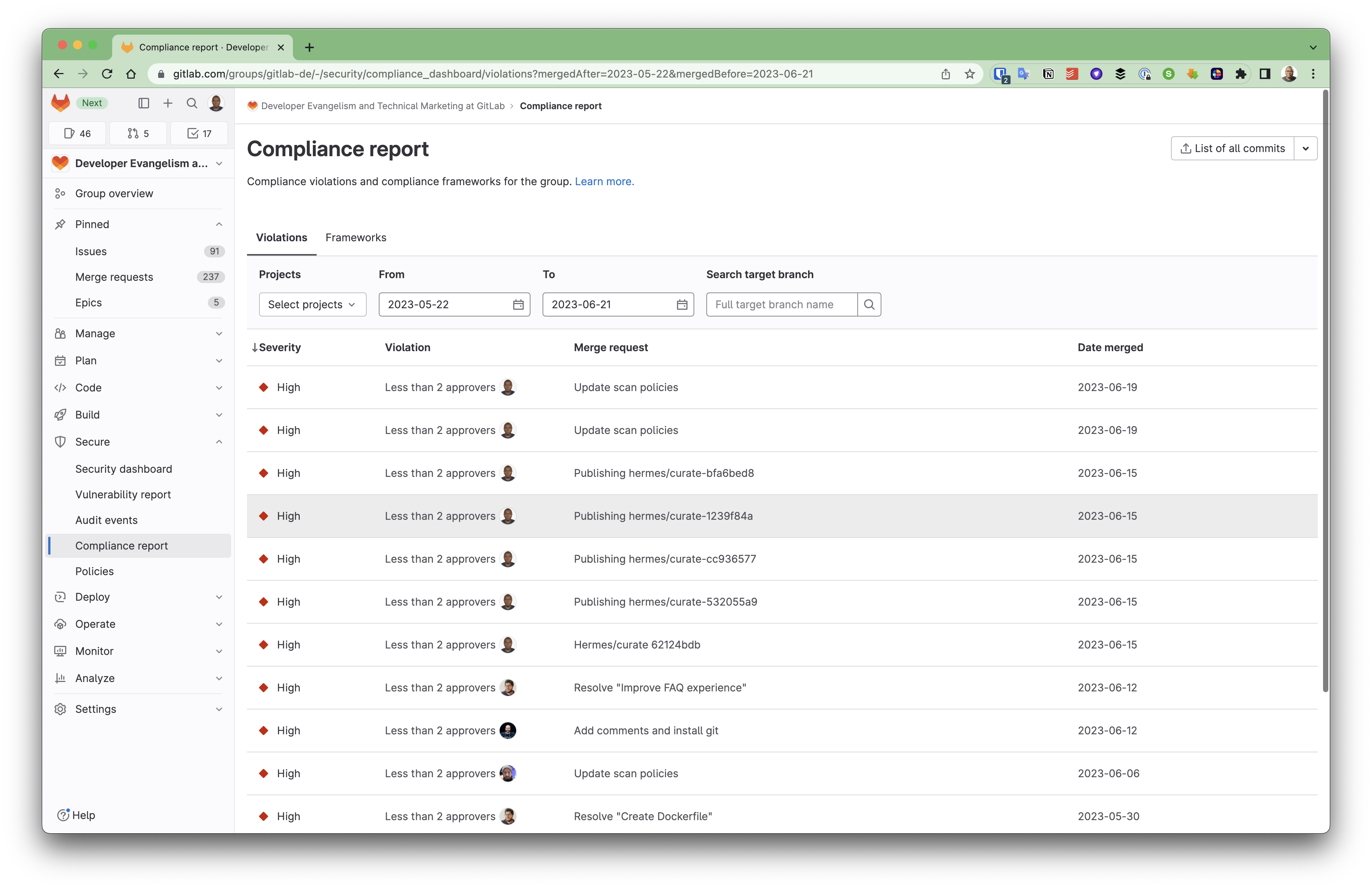
An example of compliance frameworks report for all projects in a group
Audit events streaming
Most organizations have existing systems to monitor activites in their systems in real time. With audit events streaming on GitLab, you can integrate third-party solutions like Splunk infrastructure monitoring or DataDog streams monitoring service, for real-time audit events analytics. All audit events data are sent to streaming destination (it's important to stream to a trusted service). Audit events streaming can be configured at top-level groups and, from GitLab 16.1, you can configure the feature at instance level on self-managed GitLab instances. The feature is disabled by default and will require a self-managed instance administrator to enable it with the feature flag instance_streaming_audit_event.
Learn more
Compliance is a continuous process of efficiently managing risk by implementing guardrails and monitoring compliance metrics. GitLab empowers organizations to fulfill regulatory standards with our compliance management features, which helps you build secure software and maintain the trust of your users, clients, and community. You can learn more about compliance and security policy management with the GitLab DevSecOps tutorial, which contains lessons covering the complete application security lifecycle in GitLab.



